When identities are targeted, IAM becomes the first layer of protection.
Identity and Access Management
In today’s hyperconnected digital landscape, Identity and Access Management (IAM) is the foundation of secure operations, ensuring the right access to the right people at the right time. As cloud adoption and remote work expand, identity becomes the primary attack surface. Our IAM solutions provide centralized control, authentication, and governed access across cloud, on-premises, and hybrid environments, enabling security and compliance for organizations.
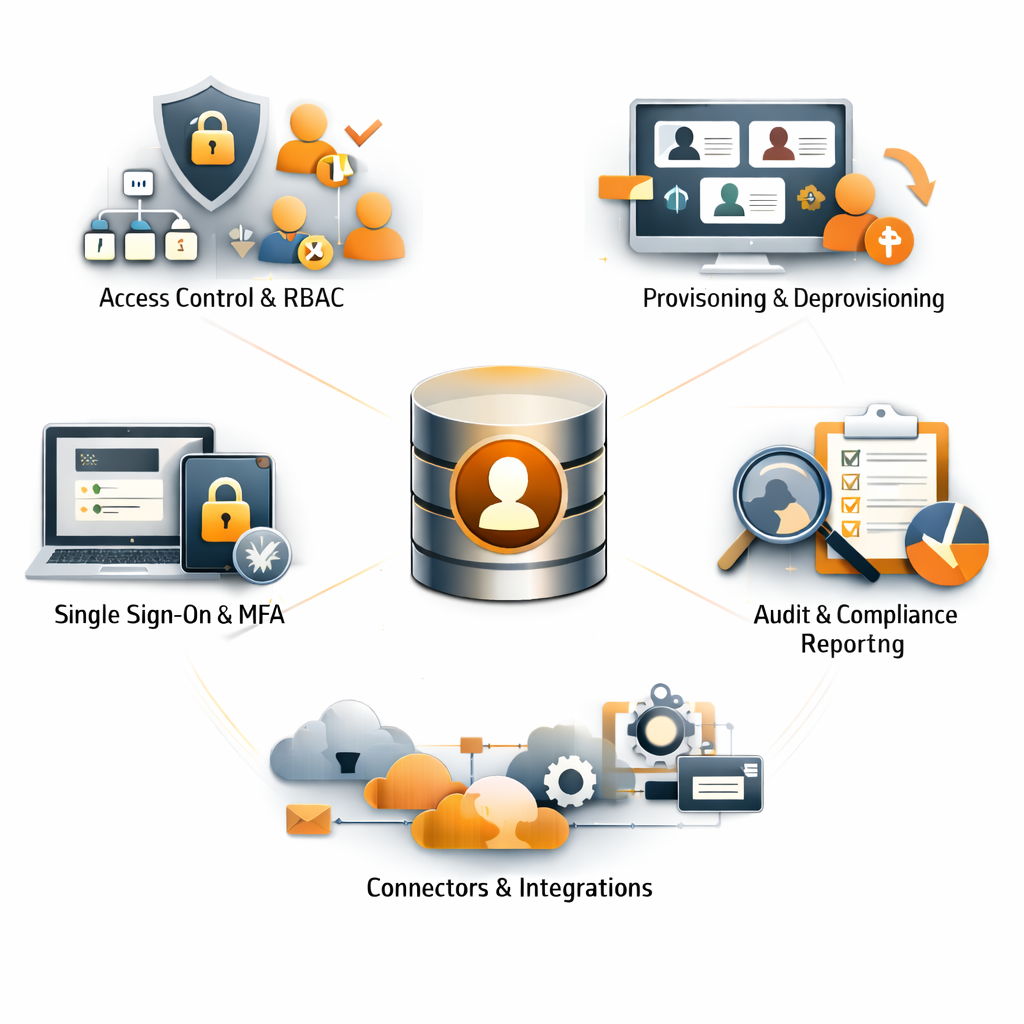
Key Features
Centralised Identity Store
Access Control & RBAC
Provisioning & Deprovisioning
Single Sign-On & MFA
Audit & Compliance Reporting
Connectors & Integrations
Why IAM Matters
Translate identity controls into measurable security, operational, and compliance outcomes for your organisation.
Reduced Identity Risk
Limit unauthorised access, stale accounts, and privilege creep across users, apps, and data.
Faster Onboarding & Offboarding
Give people the right access from day one and remove it instantly when they leave or change roles.
Improved User Experience
Enable secure, simple sign-in to critical applications so employees can focus on work, not passwords.
Stronger Compliance Posture
Meet regulatory and internal control requirements with clear visibility and evidence of who has access to what.
Operational Efficiency
Reduce manual effort for IT and HR teams with automated, policy-driven access management workflows.
Foundation for Zero Trust
Use strong identity controls as the core of a Zero Trust security architecture across your estate.
Testimonials





